 Bitcoin
Bitcoin
Regulatory attention on Bitcoin & privacy techniques to counter
Attention is both a curse and a blessing. On the one hand, almost every Bitcoiner wants more adoption and welcomes any coverage that might attract one or two new users to Bitcoin. After all, the peaceful revolution to separate money and state can only succeed if more people join it. On the other hand, not all attention is equally helpful. When Wikileaks started accepting Bitcoin donations, Satoshi was concerned about the attention given to Bitcoin in 2011 and disappeared a short time later with the following penultimate words:
“WikiLeaks has kicked the hornet’s nest, and the swarm is headed towards us.”
Satoshi Nakamoto
Today we know that the hornets went after Wikileaks (and continue to do so to this day). Bitcoin however, went on a honeymoon phase in which the network grew to a sizable strength with millions of users and institutional investors piling in. But this honeymoon phase is bound to end eventually.
In this article we will outline how increased attention to Bitcoin and accompanying regulation plans are creating an environment that is detrimental to user’s rights to financial privacy, and which Bitcoin tools to mitigate are available today.
While governments may accept that Bitcoin isn’t going away, it is extremely unlikely that they will embrace its Cypherpunk qualities of censorship resistance, financial privacy and inclusivity. More likely, they will exhaust all means to regulate the ecosystem in ways that aim to dilute Bitcoin’s censorship-resistance and put the financial privacy of Bitcoin users at risk.
Efforts to this end are already underway. The emergence of mining pools with blacklists that only want to accept compliant transactions into blocks gives an idea of how an attack on censorship-resistance could play out.
Playing right into this, are regulatory efforts, such as the recently published Financial Action Task Force draft (summary). It aims to undermine the pseudonymity of Bitcoin addresses with even broader collection of KYC data. What these regulatory domestication attempts have in common is that they attempt to exploit the public nature of the Bitcoin timechain by augmenting it with toxic honeypots of personal data.
Surveillance companies are enemies of a free society
Centralized service providers in the Bitcoin ecosystem are obliged to conform to AML / KYC regulations on a “best effort” basis and by implementing “reasonable procedures” to prevent money laundering.
The uncertainty about what “best effort” and “reasonable” exactly means is creating an environment where service providers are susceptible to the marketing of surveillance companies. These are positioning themselves as the silver bullet to regulatory compliance and consulting the service providers on “risk management” in ways that are overreaching and pre-compliant. Several companies with big marketing budgets have specialized in this kind of surveillance activity and built a business around selling on-chain snooping software and data.
Bitcoin is not anonymous, at least not by current majority default usage. The Bitcoin timechain is an open, transparent, pseudonymous public ledger accessible for anyone. It doesn’t contain any real world personal identity data, but the way Bitcoin is currently transacted by the majority of users makes it possible for observers to trace transactions and cluster addresses to entities. Should one of the addresses from a clustered entity make a transaction to a KYC exchange, the entire cluster, with all of its balances and transaction history, can be tied to a real world identity. Augmented with metadata acquired by KYC services, transactions and addresses can be mapped to identities, turning the pseudonymous timechain to a database of who owns what and who paid who. This is highly dangerous. With the latest big data analysis software, a government could sift through bulk financial data to create profiles of users, enforce a police state or engage in social engineering; criminals could seek out wealthy victims to target, companies could snoop on their employees spending behavior.
“No one shall be subjected to arbitrary interference with his privacy”
Universal Declaration of Human Rights
Privacy is a fundamental human right, essential to autonomy and the protection of human dignity, serving as the foundation upon which many other human rights are built. If intrusive surveillance companies are allowed to continue their malpractices with further adoption of Bitcoin, this could become a threat to personal safety, human dignity, the operation of a free market and ultimately, a free society.
“The way rights work is, the government has to justify its intrusion into your rights.”
Edward Snowden
Edward Snowden’s revelations have demonstrated that the right to privacy is not something humans can trust their governments to enforce. Weighed up against international terrorism, human rights have always drawn the short straw. The direction that international regulations led by FATF are headed prove once again that users cannot rely on institutions to protect their rights, that corporations and regulators cannot be trusted to safeguard the human right to privacy.
“We must defend our own privacy if we expect to have any.”
Eric Hughes
Bitcoiners know that freedom is fought for and earned. Consequently, users need to take matters into their own hands and arm themselves with defensive technology and best practices to safeguard their privacy with free code. On paper, privacy is a human right. But in reality, it’s a human fight against ever more data and control obsessed corporations and authorities.
Discovery of Coinjoin
While traditional banking provides a fair amount of privacy by making identities and their transactions only known to the trusted third party, Bitcoin inherently separates identities from transactions which are public.
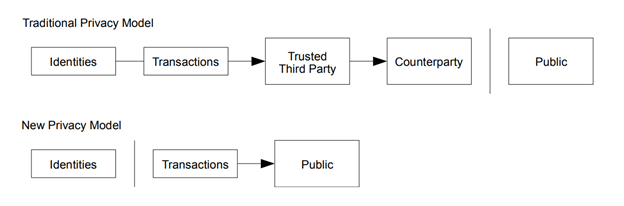
The data applied by surveillance companies and KYC exchanges aims to abolish the identity-transaction separation. To this end, they cluster addresses using the common input ownership heuristic, which is the assumption that if a transaction has more than one input then all those inputs are owned by the same entity. As of early 2021, very commonly this assumption is true, which is why surveillance companies can apply it successfully.
Thankfully, Satoshi designed Bitcoin in a way that the protocol holds solutions against surveillance attacks. Heuristics can only be meaningfully applied if they hold true significantly more often than not. When the number of false positives exceeds a certain threshold, the heuristic becomes unusable. In Bitcoin, this can be achieved by changing the way that users create transactions. The blueprint for this change was laid out by Gregory Maxwell in two BitcoinTalk posts (here & here).
“This message describes a transaction style Bitcoin users can use to dramatically improve their privacy which I’ve been calling CoinJoin.”
Gregory Maxwell
In 2013, Maxwell proposed Coinjoin, a way of transacting Bitcoin that makes it difficult for observers to determine who paid who and which output belongs to whom. To that end, multiple spenders coordinate to combine multiple inputs into a single transaction. This happens completely trustless, meaning users always keep custody of their bitcoin and do not have to trust a third party.
Herein lies a key difference to custodial mixing services or tumblers, where users must trust that the third party they sent their bitcoin to is honest and sends another party’s coins back as agreed.
But even if the mixing service is well-intentioned and they send someone else’s coins, the coin’s history will remain attached to it, now traceable to the new owner.
In comparison with mixing services, Coinjoin is therefore clearly superior as it is more akin to melting many inputs to brand-new outputs, with each of their histories detached.
Lastly, no party must take custody of any other party’s coins and run the legal risk of being classified a money transmitter or virtual asset service provider – a classification that introduces the regulatory burden of being obliged to collect personal data and employ the above mentioned “best effort” to comply with AML laws.
Coinjoin transcations have been possible since day 1 of the protocol, but were limited due to their complexity, and only used by a few who understood the craft of rolling up transactions. However, there has always been a consensus that this type of transaction should be made easily accessible to a larger number of users as Bitcoin adoption progresses.
A bounty pool with the purpose of promoting research and development for Coinjoin (currently holding 30 BTC) attracted numerous developers to this task, and shortly thereafter, the first privacy-focused wallets emerged. In recent years, usability has steadily improved and Coinjoin has ousted custodial mixing services, establishing itself as the go-to technique in the best-practice repertoire of privacy-conscious users. The implementations most broadly in use are currently Joinmarket, Wasabi Wallet and Samourai Whirlpool (overview). All three enable users to coordinate equal-output Coinjoins to break links to transaction history and increase the fungibility of their bitcoin.
However, the increase in use of Coinjoins has caused a dystopic reaction from exchanges advised by surveillance companies. Since late 2019, there have been reports of exchanges creating friction for users who used Coinjoin, hassling them with questions about the source of funds, the reason for Coinjoin usage and demanding other accounts.
Coinjoins can reliably obfuscate the transaction history, but it is possible for an observer to identify that a specific output was involved in a Coinjoin by the multiparty equal-output transaction visible on-chain.
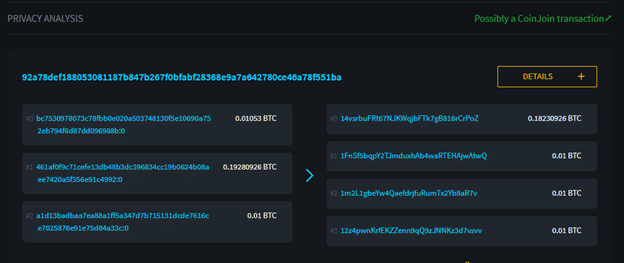
There is no specific legal requirement in any jurisdiction to flag Coinjoin use or deny service to Coinjoin UTXOs. It is simply more convenient for legislators to enact vague regulations and keep the ecosystem guessing. This way, virtual asset service providers have to anticipate what might be against the law and, in order to minimize the risk of license revocation, implement much more restrictive policies.
“We completed our compliance review and determined to ban your account with Paxful as it’s beyond our risk-appetite. We understand your privacy concerns, but the substantial amount of funds from the Wasabi wallet is high-risk for Paxful.”
Paxful
If a legislator were to attempt to define when a Coinjoin transaction should be rejected, it would have to answer the question of how many hops must be between a supposedly sanctionable transaction and its transfer to a regulated exchange for the exchange to be allowed to service it or not. However, once such a definition takes place, everyone would know how many hops it would take to fall off the grid. Regulation would therefore be tantamount to an instruction to circumvent that very regulation. By keeping the rules vague, the legislator conveniently avoids this situation at the cost of blameless users, who, stigmatized for the use of best practices, find it more difficult to secure their right to personal data protection.
“For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good.”
Eric Hughes
At this point, it must be noted that privacy coins like Monero are in no way better off than Bitcoin transactions in this regard. According to the (flawed) logic applied for Coinjoin flagging, every Monero transaction would be flagged as conspicuous. After all, the problem is not a technical one, but a social one. The only way out of this mess is to collectively honor the need for financial privacy and stop playing with those, who don’t.
Make every spend a potential Payjoin
Another very promising tool in the fight for on-chain privacy is Payjoin. It is a special type of Coinjoin transaction between two parties where one party pays the other. The major benefit of a Payjoin transaction is that it is indistinguishable from regular transactions that surveillance companies apply the common-input ownership heuristic on, but in the case of Payjoin, the heuristic fails.

In a regular transaction surveillance companies assume that all inputs belong to the payer and cluster the sending addresses to the same entity. But this assumption is broken with a Payjoin, because here one input belongs to the payee. Since it is impossible to differentiate Payjoin transactions from regular transactions with multiple inputs, also called steganographic transactions, the most powerful heuristic employed by surveillance companies to deanonymize users is broken and becomes unusable if adopted more broadly.
Here, adoption doesn’t necessarily mean that users actually use Payjoin for every transaction – for the common-input ownership heuristic to become unusable it would theoretically be sufficient that enough wallets implement this feature in a way that it becomes probable that users could have potentially used it. If enough wallets adopt Payjoin, surveillance companies are forced to adjust the success probability of their heuristics to a degree that interpretation becomes ambiguous.
The Bitcoin Wiki has a site that tracks adoption of Payjoin in wallets. Driving adoption for Payjoin is a particularly low-hanging fruit for more on-chain privacy as it doesn’t require that everyone uses it for everyone to profit from it.
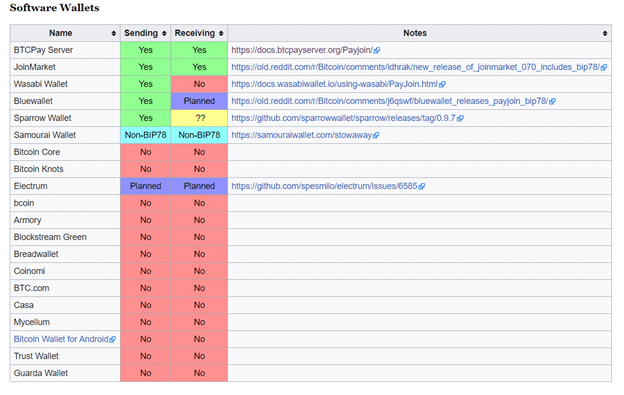
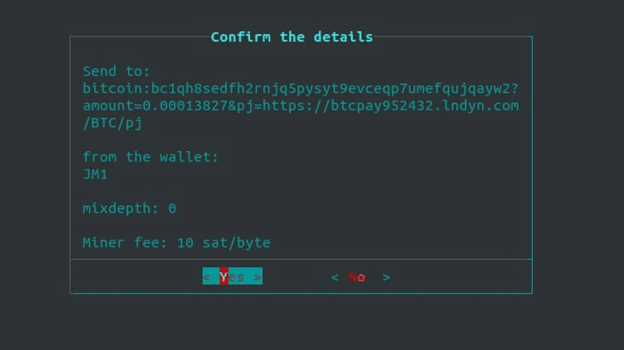
Censorship-resistance is Bitcoin’s most important property that many other fundamental properties directly rely on, but censorship-resistance itself relies partly on fungibility. Breaking the common-input ownership heuristic would be a crucial win for more fungibility in Bitcoin, and consequently for all other Cypherpunk properties. Payjoin adoption made a big step forward when JoinMarket and BTCPayServer implemented it. If only a few more would follow, on-chain privacy could benefit asymmetrically.
Of course, the mere presence of the Payjoin option in wallets does not entirely suffice. It also needs to be used. In the next article we will therefore guide you through the process of setting up Payjoin as a BTCPayServer merchant and how, as a customer, you can Payjoin with JoinMarket.
Written by @_pretyflaco, thanks go out to @HillebrandMax and @fulmolightning for input and advice. Featured image from https://en.bitcoinwiki.org/index.php?curid=271660